Social engineering
In the real world, engineering a cyber attack is far more difficult than simply lying to people, and the information gained by lying can be far more potent. And if this attack vector is left open, the value of digital security hygiene becomes little more than pageantry. Why bother trying to hack a password vault when one can simply make a phone call and lie?
Your Phone
For most people, there is a gapping social attack vector enabled by their cell phone provider. This is because our phone number is our personal identifier to the people we interact with daily. Not a PGP key or another high-quality technical id, but they recognize your phone number when you call or text. Therefore, if an attacker can gain control over your phone number, they can credibly spoof your identity to many entities, such as banks, personal friends, and even family. Furthermore, once the attacker controls this critical identifier (i.e., your phone number), they can use it to engineer further access to your accounts and cause cascading security failure.
This attack typically takes the following form. The attacker simply calls your cell phone service provider, pretends to be you, and convinces a low-level service employee to move the phone number to a new sim card under the attacker’s control. This attack works because low-level employees often fail to follow proper identification protocols and because most people use their sim card-assigned phone number for their daily interactions.
The defense
Defending from this attack demands that the phone number attached to your sim card not be the phone number used to identify you in daily life. However, accomplishing this is not straightforward. There are several ways to do this, but we recommend the most straightforward and accessible approach via Google Voice.
The goal is to have your everyday phone number controlled by you in Google Voice and secured by your Google Account, thus moving the vector from a social attack to a technical one. You then store the sim card number provided by the cell phone service provider in a safe place and forward the Google Voice number to the sim card number. By doing so, you can use the Google Voice number as if it was native to your phone while never revealing the sim card number.
In this configuration, if an attacker manages to convince your service provider to move your phone number to a sim card under their control, they can at best receive a phone number that no one would ever recognize as yours, thus blunting the attack. Additionally, you don’t lose access to the phone number you use daily, as it remains under your exclusive control. Even during the attack, you remain reachable and able to call others from the number that identifies you.
There are additional benefits to this configuration. You can make and receive calls and texts from any browser, lost or damaged phones pose no obstacle, and changing service providers doesn’t impact your life in a typical way (i.e., your number does not change). Furthermore, it’s just a good idea to have actual ownership over the critical bits of one’s identity instead of leaving it to whatever entity is powering your sim card at any given moment.
Implementing the defense
Implementation is quite tricky and will take a few days to complete. For the sake of these instructions, consider the current number on your sim card (the one people know as yours) to be your “id-number,” and the new phone number you will install (which will only be known to you and your service provider) as your “secret number.”
Step 1. Port your id-number to Google Voice. This should be done while a qualified tech support representative from your service provider is on the phone. If the process is not done correctly, you can lose your phone number permanently. Porting requires you to enter the Google Voice legacy UI and the incoming id-number while the tech support representative “releases” the id-number from the service provider’s control. At the same time, your service provider will assign your sim card a new secret number. Doing so may be considered closing and reopening your account with the service provider. However, this is just an implementation detail of how some companies structure their contracts and nothing to worry about.
Porting can take up to 4 days to complete; during this time, you will not be reachable at your id-number with any reliability as the number migrates from the service provider to your control in Google Voice. It’s also possible to port landline numbers to Google Voice, but this takes even longer and requires even more steps. However, once the porting is complete, you will be able to make and receive calls and texts from your id-number with Google Voice.
Step 2. Store your new secret number in a password manager or on paper in a safe. You should never share this number with anyone. It should be known exclusively by you and your service provider.
Step 3. Bind Google Voice to your phone. This is done by installing the Google Voice app from the App Store and signing into your Google Account. During this process, you will be prompted ONCE to “use Google Voice for all calls on this phone.” This is the option you want. If you fail to select this at the prompt, you will need to uninstall and reinstall Google Voice to get the necessary prompt.
You should use the Google Voice app to place calls instead of your phone’s native phone app from this point forward. This is an intense binding into your phone’s OS that should make the experience of using Google Voice nearly transparent for you as a user, where things “just work” as they did before.
The result is that little has changed for you as a user, but the most significant attack vector in your life is now closed.
Phishing
Detecting email phishing attempts is also important to ensure you don’t fall victim to phishing scams.
Email clients increasingly do a good job of filtering these out automatically, but it remains far from perfect. It’s a good idea to familiarize yourself with how to identify phishing attempts and provide this training to those close to you in your personal and business network. If a scammer can phish information from a loved one or a colleague, it can provide one step closer to compromising one of your accounts. Recognizing phishing attempts is everyone’s responsibility.
Multi-Factor Authentication
The definition we are going to use for Mutli-Factor comes from NIST SP 800-63-3. The three authentication factors are:
🧠 Something you know
🔑 Something you have
☝ Something you are
One simple real-world example in which we have all engaged with these 3 factors is when you walk into your local bank. The banker recognizes your face (something you are) but still needs you to provide your bank card (something you have) and enter the pin (something you know).
🧠 Something you know
Something you know is the first factor of authentication and is typically considered the most important. This is commonly known as passwords or passphrases.
Passphrases
Setting up a security question with every professional entity you communicate with over the phone is a good idea. When you call, the operator must ask you this question and receive the correct answer to proceed with the call. It’s worth asking about, and most companies support it but do not advertise it. Furthermore, some companies support an implicit phrase, as in you must state the passphrase without their prompting. And the implicit phrase is the best security you can get, as an attacker won’t even know why they are being rejected. Instead, the operator just hangs up if the caller doesn’t say the passphrase within the first couple of sentences. Of course, there is no guarantee that the operator will follow the protocol, but having it in place is better than nothing.
Implementing passphrases
There isn’t a surefire way to implement passphrases across all the companies you do business with. You just have to make it a habit. The best way is to attach a note to your phone to remind yourself to ask about security questions and implicit passphrases as you end up organically calling different companies.
Online passwords
Each account you have online should have its own password, and it should be as strong as possible. To make this problem tractable, you will need to use a password manager, such as 1password, Dashlane, or similar secure software. At this time, I recommend 1password, as it’s cross-platform and has exportable, as well as shareable, vaults. Sharable vaults are an essential feature if you want to share secrets with others securely.
A password per account
Different accounts have different password recipes, consisting of a minimum requirement and a maximum requirement. The minimum requirement is typically easy to meet, but the maximum requirement often is not. As such, generating the strongest possible passwords takes some trial and error. However, if you can get a 32-character password with capital and lowercase letters, numbers and symbols, you are in fine shape and probably don’t need to figure out the actual maximum. However, some services have maximums that are more restrictive than this, so trying for 32 characters and getting rejected will help you find the actual maximum recipe. Passwords should be generated inside your password manager and copied from there when setting your password for the first time.
What about my Netflix account; surely that one doesn’t matter?
Some accounts may seem unimportant for security, and you might be right. But can you afford to be wrong? Attackers are incredibly creative and will find whatever point in your personal security mesh is weakest to attack. Maybe some accounts don’t matter, but figuring out which ones those are, and monitoring them to see if their status changes in the future, is an insurmountable task. As such, you should not leave even the most trivial accounts unsecure. No exceptions.
Implementing password hygiene
Unless you already are using a secure password manager, with a unique password per account, you likely have some very weak passwords, or some passwords stored in your OS or browser password manager. You should delete everything from your browser or OS password system. These are not secure password managers, and deleting everything will force you to go through a password reset on each account as you try to access it. When resetting, you will of course generate the passwords in the password manager as described above. Any passwords that are so weak that you have them memorized need to be updated immediately.
Choosing a quality master password
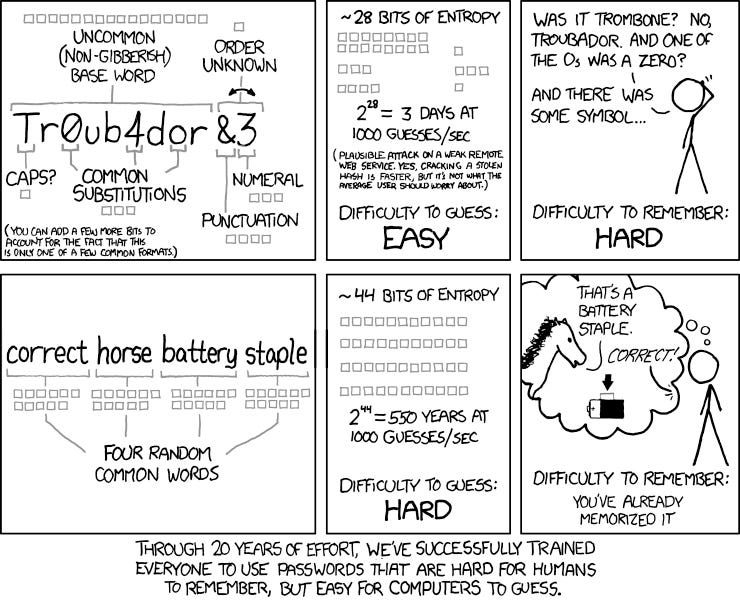
A password’s quality is determined by the entropy, or randomness, contained therein. The following comic illustrates the principle.
XKCD Source Words have the highest entropy. This is partly why passphrases composed of multiple words are such an excellent choice for blockchain and are used in most blockchains as part of the security protocol. As the comic above illustrates, using multiple random words makes remembering the password easy for humans, but guessing the password is difficult for computers. This is good because you will need to memorize your master password.
Additionally, the presence of some symbols can add some additional protection. For example: “The question is who is to be master” is less secure than “1he question i! who is to b? master”. If you must write your master password down, it should be stored in a safety deposit box or in the care of your attorney. Having a physical copy of your master password is wise if you are concerned about the potential of a divorce or your next of kin having access to your accounts in the event of your death.
🔑 Something you have
Something you have is the second factor of authentication, sometimes called 2FA. However, many methods called 2FA today do not actually count as security by something you have. For example, if you use 2FA with 1password, you are not actually using something you have; you are just converting your account’s 2FA functionality to something you know. And two layers of something you know does NOT constitute the second factor of authentication. In fact, by securing these with the same master password, exactly zero additional protection has been gained.
Questionable 2FA
Some techniques referred to as 2FA may or may not be 2FA in practice. For example, email-based 2FA where the authentication provider emails the user a one-time pass. The user then enters that one-time pass to gain access. This technique does not actually provide 2FA; what it does is transfer the security properties of their system to your email. Meaning: if your email is secured by 2FA, this one-time pass is therefore secured with 2FA via the transitive property. However, if your email is NOT secured with 2FA, then this technique does not provide an additional factor of authentication.
This is also true with SMS-based 2FA. If your SMS access is secured via 2FA, then the SMS-sent pin is also secured with 2FA via the transitive property. However, this is rarely the case; instead, the theory is that the second factor is provided by the physical access to your phone, which receives the message. To make matters worse, SMS is usually not even encrypted on the wire, so the one-time pass can be easily intercepted by a third party. Given the physicality is not guaranteed, and that messages are sent unencrypted over a wire, this is the weakest technique referred to as 2FA.
Please Note: Some services recommend you use a weaker form of 2FA as a backup to a stronger form. For example (Discord asks you to set up your phone as backup), do NOT do this. Your security is only as strong as your backup and recovery.
TOTP
Most forms of strong 2FA are in the form of a Time-based One-Time Pass (TOTP). Some examples of this are the Google Authenticator, Authy, and hardware TOTP devices like Digipass. TOTP is a private key that can be used to generate a time-based, one-time password. The authenticator can then check that this short-lived password validates the account and permits access.
App-based
Apps such as Google Authenticator and Authy turn your phone into something you have, as the private key for these codes (transmitted via QR code in most cases) is stored locally on the device. Now to authenticate, an attacker needs physical access to your device, or so the theory goes. While Google Authenticator is theoretically secure in its storage of your private TOTP key, it is still a software application living on a computer (i.e., your phone) connected to the internet. And that is not ideal.
FIDO keys
A better approach is to procure a FIDO key, such as a YubiKey. These are hardware devices designed to store secret keys securely. Peer-reviewed research suggests that it’s intractable to read a private key off a FIDO key. Additionally, this technique has been battle-tested at scale by large organizations such as Google, where breaches due to authentication attacks fell to zero upon implementation. After this experience, Google opted to create their version of a FIDO key, known as the Titan Key, to avoid paying Yubi for access to the technology.
UFA
FIDO keys offer an even more robust method of 2FA via TOTP, known as Universal Two-Factor Authentication (UFA). This technique allows the physical FIDO key to communicate directly with the authentication provider, proving you have physical access to the key. This method is more robust than TOTP on FIDO, because the private key is never transmitted unencrypted via a QR code, and there is no one-time pass to steal; authentication is instant. Using this method is also more convenient than TOTP, as you merely have to touch the FIDO key to authorize communication, rather than entering a one-time pass.
Other hardware
FIDO keys are forms of Hardware Security Modules (HSM). There are others, such as hardware wallets for crypto and the chip on your credit card. HSMs are a proven technology in traditional finance and are considered standard. For example, your debit card is a form of 2FA, as using it to access your account requires a pin (something you know) and the HSM chip of the card (something you have).
Implementing 2FA
You should use the strongest 2FA possible for each online account that supports it. You will need to obtain at least 2 YubiKeys or comparable FIDO keys. This is because YubiKeys cannot be duplicated. So in order to have a backup, you must add private keys to both keys at the same time. I recommend starting out by going through your password manager, visiting the security section of each account, and adding 2FA wherever it’s available.
After logging into an account that uses TOTP, you will first turn off 2FA, then re-enable it. Doing so will cause a QR code that holds the TOTP private key to appear. At this time, you will grab the code with both YubiKeys and NOT save the recovery codes. If you cannot access one of your YubiKeys at this time, you can copy the “manual code” into your password manager. When you have access to the backup YubiKey, you can add that TOTP via the “manual code,” and then remove it from the password manager.
Remember, in this configuration, if you lose all of your YubiKeys, you are permanently locked out of your account. This makes sense if you consider these are now acting as physical keys.
Some services support UFA, which should be preferred when available. Examples of such services are Google and GitHub. Over time, we expect more online services to support UFA. Google UFA is particularly useful, as it can be used to enhance the security of questionable 2FA techniques. For example, the combination of an email-based, one-time pass and GMail means this pass receives UFA-level security via the transitive property; the same goes for the combination of SMS-based, one-time pass, and Google Voice (which also encrypts SMS messages).
☝Something you are
Something you are is the third factor of authentication and can take many forms. On the social side, we have the recognizability of your voice, your face, even your gait to people who know you well. Another human’s ability to identify your physical presence is a form of third factor. On the technical side, we have various forms of biometrics, from fingerprint and iris scanners, to facial recognition, to a blood sample.
Most services don’t offer a third factor, but it’s a good idea to use it for those that do. For example, if you use the latest version of the YubiKey, it can strengthen the key by reading your fingerprint to authorize the key to communicate.
Overall, two authentication factors are typically enough, so don’t feel bad when only a few services you use support biometrics. However, biometrics alone constitute strong authentication, even without the other factors, as it limits access to you physically. The only potential for failure here is spoofing the sensor, which varies in difficulty depending on the form of biometric. Fingerprint scanners are more challenging to spoof than facial recognition, for example.
Implementing biometrics
In practice, implementation will mean using the fingerprint scanners on your hardware to unlock it, such as your phone and, potentially, your laptop. To add biometrics to your 2FA solution, buy the YubiKey 6 with the fingerprint reader enhancement.
Email recovery
Typically when you sign up for an email account, you will be required to provide a backup email address to recover your account. This can be a point of vulnerability. For example, if an attacker can access the backup email and trigger a recovery on your primary email account, they can gain access. Even if you have three factors of authentication on your Google account, this can all be bypassed if the backup email is not secure. As such, it’s a good idea to set up a recovery loop. This means that your primary email address has a recovery email address that is just as secure. And the backup email account should have the recovery email address set to your primary account. Setting up a loop like this ensures that the security on your email account is not weakened by softer security on the backup account. Your email security is only a bit stronger than the weakest security of an email in the recovery chain.
Lead pipe attack
So now you are protected from social engineering attacks and secured with multiple factors of authentication. There is still one kind of attack we just can’t stop, and that is when someone either threatens or attacks you or a loved one physically. This scenario is one where you may be inclined to grant the attacker access to accounts yourself for obvious reasons. These kinds of attacks are best handled by local law enforcement, but some planning can be done. Home security systems, self-defense training, and your bodily health can all play a role in making the lead pipe attack harder to pull off.
Distributed responsibility
Distributing the responsibility to access certain authentication factors can be a great way to blunt a lead pipe attack, but should only be done for the most sacred of keys. For example, a blockchain passphrase can be chopped up and sent to trusted locations (like a safe deposit box) or individuals (like an attorney or sibling). A distribution that is too broad increases failure points, where if an individual in the trust network becomes unreachable, everyone may be locked out of access. Too narrow a distribution makes a lead pipe attack more feasible, as there are a limited number of people to threaten. Designing a good trust network to distribute responsibility in a safely recoverable manner is something you should give serious thought to, and not something anyone can advise you on beyond the considerations stated here. This is about who you trust, how much you trust them, and how much pain you’re willing to go through if you need access in the future.
Death, legal incompetence, and divorce
Death and divorce are scenarios where custody of authentication factors can be transferred without your consent. You should talk through these scenarios with your attorney. Failure to have a plan for these scenarios can result in loss or even malicious parties gaining control of your assets. Having a living will and, potentially, a nuptial contract around your authentication is the last but essential step in achieving security.
SSH Keys
If you are a technical person who uses SSH keys, it’s best to do this by integrating SSH+GPG+YubiKey, where private keys are stored on the FIDO hardware and used to access SSH. Additionally, all SSH keys should have an SSH passphrase stored in your password manager; when possible, the new SK public key variants should be used, as they are the most secure.
High-level instructions
Port your phone number to Google Voice
Take phishing training and train others
Setup verbal passphrases with service providers
Delete any insecure password storage
Generate new passwords for all accounts in 1password
Purchase at least 2 YubiKeys with biometrics
Replace any app-based 2FA with the YubiKey TOTP (do not use SMS as a backup, even if recommended)
Add the YubiKeys for UFA on critical accounts
Use the fingerprint scanner to unlock your phone or laptop
Setup email recovery loop
Design your trust network for sacred authentication
Talk to your attorney about involuntary custody transfer events
It can be a good idea to put this into a spreadsheet, and not some top-level categories of account types, so you have something to check off as you progress. Good luck! Stay safe out there!